divineomega/laravel-password-exposed-validation-rule
最新稳定版本:v2.5.0
Composer 安装命令:
composer require divineomega/laravel-password-exposed-validation-rule
包简介
Laravel validation rule that checks if a password has been exposed in a data breach
README 文档
README
This package provides a Laravel validation rule that checks if a password has been exposed in a data breach. It uses the haveibeenpwned.com passwords API via the divineomega/password_exposed library.
Installation
To install, just run the following Composer command.
composer require divineomega/laravel-password-exposed-validation-rule
Please note that this package requires Laravel 5.1 or above.
Usage
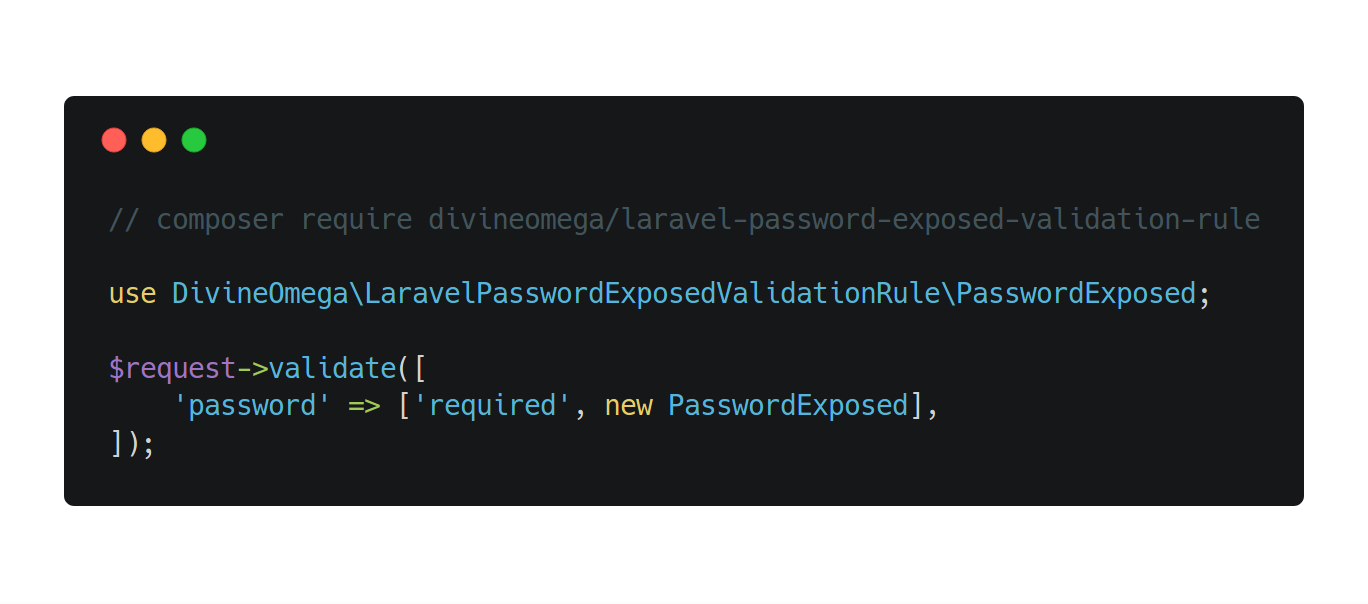
The following code snippet shows an example of how to use the password exposed validation rule.
use DivineOmega\LaravelPasswordExposedValidationRule\PasswordExposed; $request->validate([ 'password' => ['required', new PasswordExposed()], ]);
If you wish, you can also set a custom validation message, as shown below.
use DivineOmega\LaravelPasswordExposedValidationRule\PasswordExposed; $request->validate([ 'password' => ['required', (new PasswordExposed())->setMessage('This password is not secure.')], ]);
统计信息
- 总下载量: 692.99k
- 月度下载量: 0
- 日度下载量: 0
- 收藏数: 90
- 点击次数: 1
- 依赖项目数: 3
- 推荐数: 0
其他信息
- 授权协议: LGPL-3.0-only
- 更新时间: 2018-04-26